Same Origin Policy
The Same Origin Policy (SOP) is a critical security concept in web development and
cybersecurity. It is a browser security feature that is designed to prevent
malicious websites from making unauthorized requests to another website's
resources. The SOP is a fundamental part of the web security model and helps
protect users from various types of attacks, such as
cross-site scripting (XSS) and
cross-site request forgery (CSRF). Same Origin Policy security
Here's how the Same Origin Policy works:
1) Origin Definition: An origin is defined by a combination
of three components: the protocol (e.g., http, https), the domain (e.g., example.com), and the port number. Two web pages have
the same origin if these three components match.
2) Access Restrictions:
The Same Origin Policy restricts web pages from making requests (such as
XMLHttpRequest or Fetch API requests) to a different
origin than the one that served the web page. This means that JavaScript
running on a web page from one origin cannot directly access or manipulate
resources on a different origin.
3) Exceptions: There are
some exceptions to the Same Origin Policy, such as allowing resources to be loaded from different origins if
explicitly permitted through mechanisms like
Cross-Origin Resource Sharing (CORS) headers. These exceptions are controlled by the server hosting the resource
being accessed.
4) Cross-Origin Requests: If a web page
tries to make a cross-origin request without proper authorization (such as
appropriate CORS headers), the browser will block the request and prevent the web page from accessing
the response data.
The Same Origin Policy is a foundational
concept in web security that helps protect users and their data from
unauthorized access and malicious attacks by enforcing strict rules about how
web pages can interact with resources from different origins.
There are three type of origin -
1) Protocol: This specifies the communication protocol used
to access the web resource. It is usually either "http" or
"https."
2) Domain: This is the
hostname of the web server that hosts the resource. It can be an IP
address or a human-readable domain name, like "example.com."
3) Port: This is the network port on the web server that is used for communication. It
is typically omitted or assumed to be the default port (80 for
HTTP, 443 for HTTPS) unless explicitly specified.
In
simpler terms, an "origin" is a unique combination of the protocol, domain,
and port that identifies the source of a web page. For example, if you have a
web page loaded from "https://www.example.com," its origin would be
"https://www.example.com."
Lets take example of live with localhost in our
kali linux
Now, Here we creating two file, one is example1.php and another one is called example2.php but inside of example1.php file we adding iframe with src of example2.php file and then with the help of this we will access the SAME ORIGIN POLICY (SOP) (another host, domain, port, protocol).
Here is the code of example1.php
<!DOCTYPE html>
<html>
<head>
<title>Same Origin Policy</title>
</head>
<body>
<iframe src="http://127.0.0.1:9091/example2.php" name="test" width="800" height="600"></iframe>
<script>
document.getElementsByName('test')[0].onload = function()
{
try {
console.log(frames[0].hostname)
}
catch(e)
{
console.log(e);
}
}
</script>
</body>
</html>
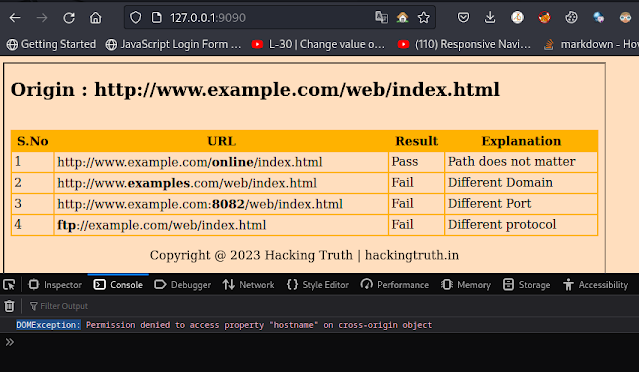
Output
Now we will open inspect element and check console and as you can see below the image
It is telling permission denied to access property "hostname" on cross-origin object so, we can't access SOP.
But if we want to access them don't worry I AM HERE -:)
Don't forgot to check out these links and go to these website to learn how to access them.
Exploitation of CORS Prefix-Suffix Match
Brought to you by
Hacking Truth
Direct Link -
CLICK HERE
Cross-Origin Resource Sharing
W3C working draft that defines
how the browser and server must communicate when accessing sources across
origins. CORS Cross Origin Resource Sharing Vulnerability on Live Website.
Disclaimer
All tutorials are for informational and educational purposes only and have been made using our own routers, servers, websites and other vulnerable free resources. we do not contain any illegal activity. We believe that ethical hacking, information security and cyber security should be familiar subjects to anyone using digital information and computers. Hacking Truth is against misuse of the information and we strongly suggest against it. Please regard the word hacking as ethical hacking or penetration testing every time this word is used. We do not promote, encourage, support or excite any illegal activity or hacking.