p0f-kali-linux
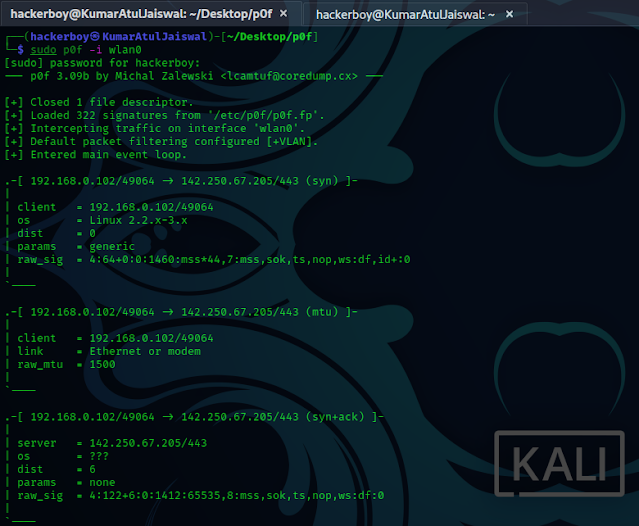
p0f performs passive OS detection based on SYN
packets. Unlike nmap, p0f does recognition without sending any data. Additionally, it is able to
determine the distance to the remote host, and can be used to determine the
structure of a foreign or local network. When running on the gateway of a
network it is able to gather huge amounts of data and provide useful
statistics. On a user-end computer it could be used as powerful IDS add-on.
p0f supports full tcpdump-style filtering expressions, and has an extensible
and detailed fingerprinting database.
To use p0f on Kali Linux, you can follow these steps:
1. Open a terminal on Kali Linux.
2.
Install p0f if it's not already installed:
sudo apt update
sudo apt install p0f
Once p0f is installed, you can start using it by
specifying the network interface you want to monitor for passive OS
fingerprinting. For example, to use p0f on the "eth0", "wlan0" network interface, you can run the following command:
sudo p0f -i <interface name>
ifconfig (To check interface in
your kali system)
The tool will start listening to the network traffic on the
specified interface and attempt to identify the OS of the hosts communicating
on that network.
Please note that network sniffing and OS
fingerprinting can be subject to various legal and ethical considerations.
Always ensure you have the necessary permissions and authorization before
using such tools, and only use them on networks you own or have explicit
permission to test. Unauthorized use of network sniffing tools is illegal and
unethical. Always act responsibly and respect the privacy and security of
others.
Disclaimer
All tutorials are for informational and educational purposes only and have been made using our own routers, servers, websites and other vulnerable free resources. we do not contain any illegal activity. We believe that ethical hacking, information security and cyber security should be familiar subjects to anyone using digital information and computers. Hacking Truth is against misuse of the information and we strongly suggest against it. Please regard the word hacking as ethical hacking or penetration testing every time this word is used. We do not promote, encourage, support or excite any illegal activity or hacking.